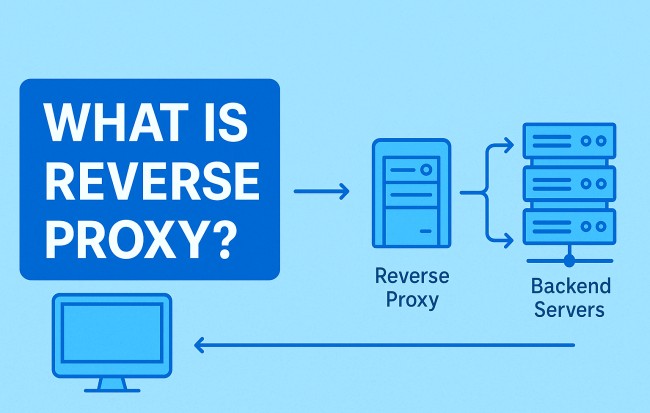
When someone utters the phrase reverse proxy, it often triggers blank stares outside of server rooms. The term sounds deceptively simple, yet its role in modern digital infrastructure is anything but trivial.
A reverse proxy isn’t merely a middleman – it’s an entire gateway, a bouncer at the club entrance, a translator in a negotiation, and sometimes even a bodyguard for web servers.
If you run apps, handle user traffic, or care even slightly about scalability and security, understanding reverse proxies isn’t optional. It’s critical.
Here in this article, we will discuss what is a reverse proxy, how it works, and why it matters for security, speed, and scaling your web infrastructure.
What Exactly is Reverse Proxy?
At the heart of it, a reverse proxy is a server that sits in front of web servers and intercepts requests from clients. Instead of users directly knocking on your web server’s door, they reach the reverse proxy first. This server then decides where to forward that request and what to hand back in return.
Think of it like a receptionist at a corporate building. Visitors don’t stroll straight into the CEO’s office; they check in at the desk.
The receptionist verifies the purpose, routes them to the right department, and sometimes says, “Sorry, you don’t have access.” That’s essentially the behavior of a reverse proxy – except digital, and often automated with extreme precision.
Contrast that with a forward proxy – which works the other way around, usually hiding the client. Reverse proxy, as the name implies, reverses that role: it shields and manages the server-side instead.
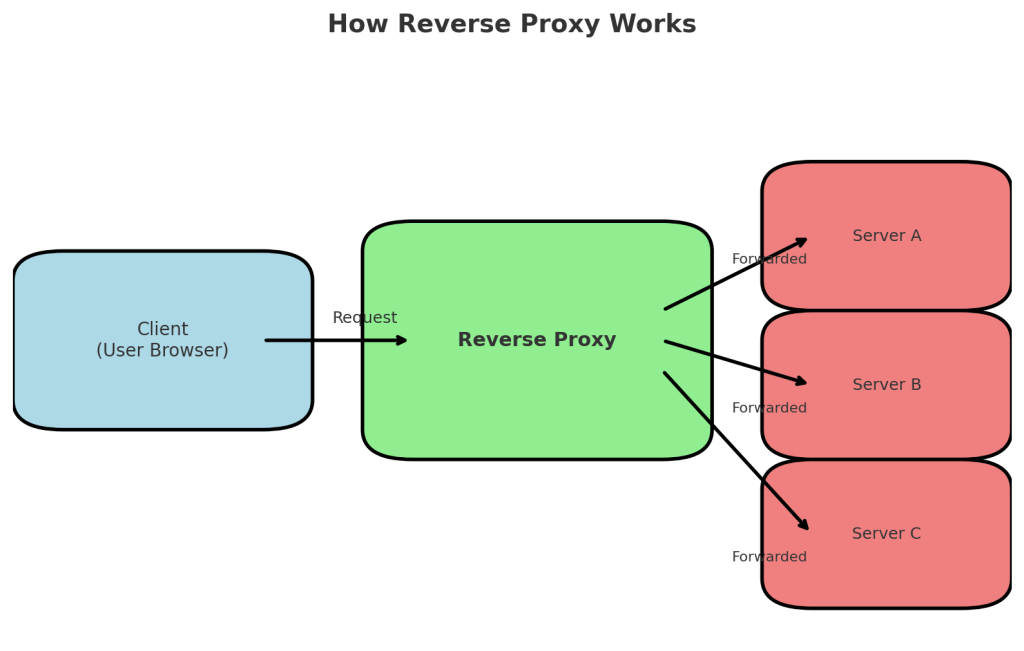
How Does a Reverse Proxy Work?
Breaking down the workflow:
- Incoming Request Lands: A user types in a website URL or fires off an API call. Instead of heading straight to the actual server, the request is intercepted.
- Reverse Proxy Receives It: The proxy evaluates where that request should go. Maybe Server A is free, maybe Server B is overloaded, maybe Server C has cached the response.
- Routing and Processing: Depending on configuration, the proxy routes the request to the chosen backend. Along the way, it may rewrite headers, add authentication, or compress traffic.
- Response Sent Back: The backend processes the request, hands the response back to the proxy, which in turn forwards it to the user. From the outside, users never even know which internal server handled them.
That’s the mechanical side. But beneath this lies a web of capabilities – from performance optimizations to cloaking sensitive infrastructure.
Why Reverse Proxy Matters for Modern Infrastructure
Without a reverse proxy, every client request lands squarely on your servers. That sounds simple, but simplicity here is dangerous. Direct exposure leads to risks, bottlenecks, and headaches.
A reverse proxy matters because it adds a buffer layer that transforms raw requests into manageable, optimized flows.
In fact, most large-scale applications – whether you’re streaming videos, managing SaaS dashboards, or running e-commerce – are already standing on the shoulders of reverse proxies. They’re the invisible scaffolding.
Let’s look at the specific benefits.
Security Shielding
One of the prime jobs of a reverse proxy is security. Exposing your real server’s IP to the public internet is a bad idea – it’s like publishing your home address on a billboard. Attackers scan, probe, and exploit. A reverse proxy masks those backend details.
Features like:
- DDoS Mitigation: By filtering incoming floods before they ever touch your servers.
- TLS Termination: Offloading encryption and decryption to the proxy instead of every backend.
- Access Control: Serving as the checkpoint for authentication or firewall rules.
It’s not just about blocking malicious actors – it’s about reducing the attack surface to almost nothing.
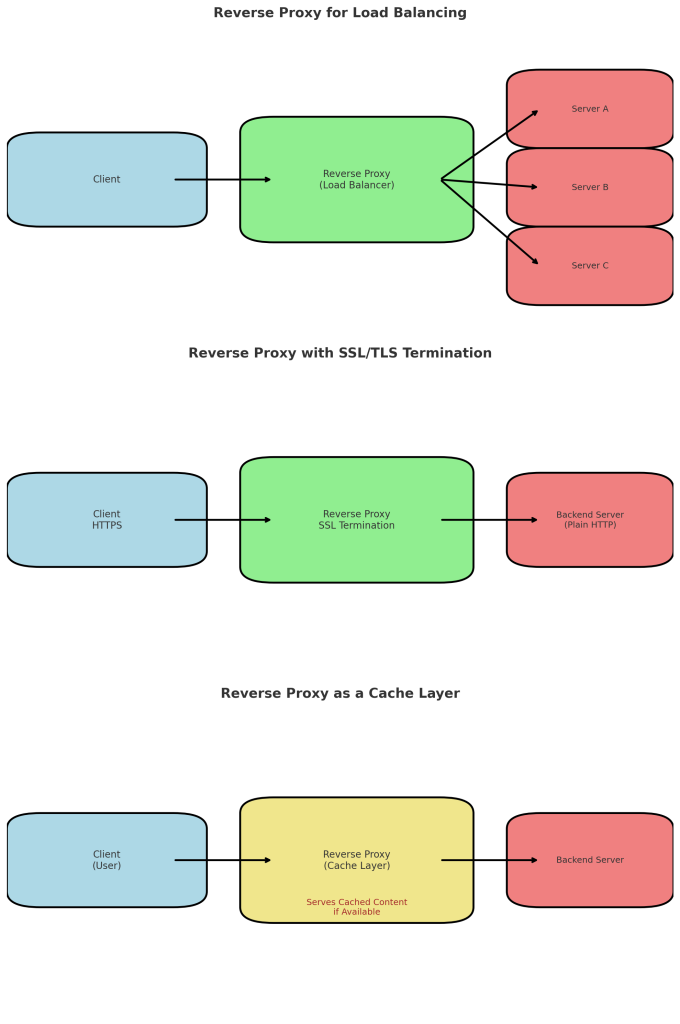
Load Balancing and Scalability
Servers are finite. Throw 100,000 simultaneous requests at a single machine and you’ll watch it crumble. Reverse proxies provide load balancing by distributing incoming traffic across multiple backend servers.
Algorithms vary: round robin, least connections, weighted distributions, and even latency-based routing. Each ensures that no single machine becomes the weak link.
This isn’t luxury – it’s survival. Without balancing, scaling applications past a few thousand users becomes nearly impossible.
Caching for Speed
Another jewel in the reverse proxy toolkit: caching. Instead of fetching identical resources over and over, the proxy can hold frequently requested content in memory or disk.
So when 500 users request the same homepage, the proxy serves it instantly, sparing backend resources. This slashes response times, saves bandwidth, and delights impatient visitors.
Caching is one of those silent heroes. Users never see it, but they feel it when a site loads in milliseconds instead of seconds.
SSL Termination
Encryption is vital. But handling HTTPS connections consumes CPU cycles. Reverse proxies can terminate SSL/TLS connections – decrypting at the edge – before forwarding plain traffic internally.
This setup not only improves performance but centralizes certificate management. Instead of juggling keys on dozens of backend servers, you handle them in one place: the proxy.
Application Firewall Capabilities
Many reverse proxies double as Web Application Firewalls (WAFs). They inspect traffic at a deeper level, identifying malicious payloads hidden inside requests. SQL injection attempts? Blocked. Suspicious patterns? Dropped before they cause chaos.
This goes beyond basic firewalling – it’s about securing the application layer where most breaches occur.
Reverse Proxy Use Cases in the Wild
Reverse proxies aren’t theoretical toys – they’re embedded in countless infrastructures:
- Content Delivery Networks (CDNs): Services like Cloudflare or Akamai essentially operate giant reverse proxy networks.
- Enterprise Intranets: Internal apps shielded behind reverse proxies to control access.
- Microservices Architecture: Acting as gateways between dozens of microservices, providing routing and consistency.
- E-commerce Platforms: Handling SSL, caching, and load balancing during traffic spikes (Black Friday, anyone?).
- APIs: Ensuring secure, scalable, and throttled access.
Wherever there’s scale, there’s usually a reverse proxy humming away in the background.
Popular Reverse Proxy Tools
The tech ecosystem brims with tools serving as reverse proxies. Some names ring out more than others:
- NGINX – Lightweight, blazing fast, and widely adopted. Handles static content, caching, SSL termination, and load balancing effortlessly.
- HAProxy – Renowned for advanced load balancing at high scale. Often paired with mission-critical workloads.
- Apache HTTP Server (with mod_proxy) – Flexible, though heavier compared to NGINX.
- Traefik – Cloud-native, designed for dynamic microservices environments.
- Caddy – Developer-friendly, automatic HTTPS, clean configuration.
Each has strengths, and the choice depends on your environment – bare metal, containers, Kubernetes, or cloud-native stacks.
Challenges and Considerations
Like every tool, reverse proxies come with caveats. Misconfigurations can open doors rather than close them. Over-reliance on caching can serve stale content. Centralizing SSL at the proxy creates a single point of failure if not properly secured.
Latency is another subtle risk. If the proxy isn’t tuned or located near users, you may introduce delays instead of improving speed. Monitoring and constant tuning are part of the game.
Reverse Proxy vs. API Gateway
People often confuse reverse proxies with API gateways. Both sit at the edge, both route traffic, but gateways add extra layers of policy, analytics, authentication, and monetization features.
Reverse proxies are the fundamental building block. Gateways are the specialized evolution. Think of it like comparing a multipurpose router to a custom enterprise appliance – one general, the other tailored.
The Bigger Picture
Step back and you’ll see: reverse proxies aren’t niche – they’re foundational. They power web scale, protect sensitive systems, and grease the wheels of user experience. Whether you realize it or not, every tap on your smartphone or click on a shopping cart probably passed through one.
In cloud-native contexts, reverse proxies evolve into sidecars, service meshes, and gateways. Yet the core concept remains unchanged: intercept, manage, and deliver requests smarter than direct connections ever could.
Final Thoughts
The next time you hear “reverse proxy,” don’t shrug it off as jargon. It’s the silent sentinel guarding infrastructure, the traffic director balancing millions of requests, and the accelerator shaving seconds into milliseconds.
Without reverse proxies, the internet as we know it would be slower, less secure, and far less resilient.
If you’re architecting systems, ask yourself: where does my reverse proxy fit in? Are you leveraging caching? Have you secured TLS termination properly? Are your load balancing strategies tuned for spikes?
Because at the end of the day, reverse proxy isn’t just about routing traffic – it’s about shaping digital experiences, enabling scale, and protecting the systems that keep businesses alive.
Also Read:

